URL: https://addons.mozilla.org/zh-CN/firefox/addon/quicker-connector/
I have replyed the email, but still no response.
Using eval is by desigin, that’s how this extension works.
Custom scripts are from users, actions triggered by users.
This extension is designed to run user defined code from ‘Quicker’ application to control webpages or browsers.
The chrome version of this extension has been released for several months and has more than 3000 installations. Link
Many users request Edge and Firefox versions. So I just made this one.
The edge version with same code also passed certification: link
Quicker is a windows software that allows users to create many actions and trigger action when they need. (Home page : https://getquicker.net)
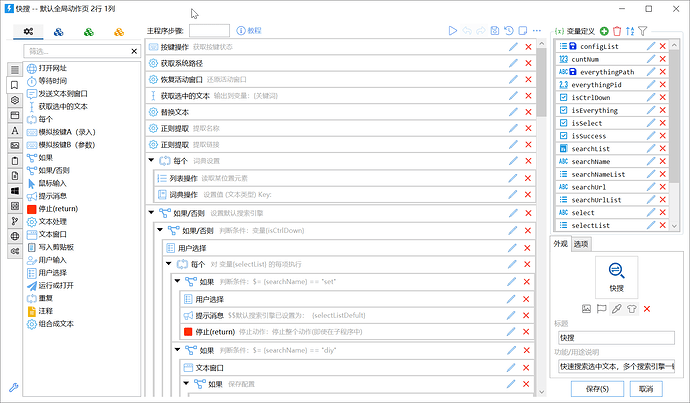
Action was built using ‘Blocks’, each Block is just like a method in programming language.
‘Browser Control Block’ is one of them. It allows users to perform automatic operations on browsers.
The extension needs to use eval to run the background script to realize these functions.
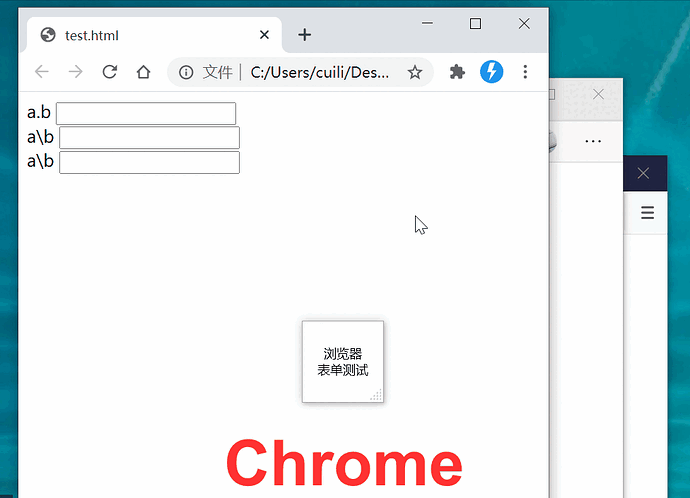
Here’s a example to fill web form:
Here is an example to control browser (close tabs on left side) :
Another sample action to sort browser tabs by title or url:
By running custom scripts, users can perform actions with great flexibility.
I have no way to change code and still make this work.
Please do not disable it, thanks.



 .
.



